24 x 7 Global Security Operations Centre
CYBER SECURITY
How can you and your team keep pace with the rapidly changing field of cybersecurity?
That's a difficult problem!

We understand that confronting cybersecurity threats is a significant, expensive challenge for most businesses.
In our experience, the problem can best be solved by outsourcing Cyber Security Operations to a well-resourced and Certified Global Team, fully focused on the task 24x7
Protecting your business against cybercrime
Maybe you are relying on your local computer guy or managed services support with off the shelf antivirus to provide cover...
It’s probably a bad idea right?
As a business leader, juggling your core responsibilities with mastering the fast-changing world of cybersecurity is too much to ask.
It's an intricate field that demands constant attention.
The significant expenses tied to self managed cybersecurity defences present another burden.
Between everyday financial challenges and these costs, the strain can be overwhelming.
Then there's the risk of a cyber-attack; the potential for financial and reputational loss and even legal troubles adds to the weight you carry.
This should not be part of your daily worry.
Facing the Challenge
Connect with our team, share your specific needs via a simple questionnaire, and we will provide tailored service and cost effective subscription options that suit your unique requirements.
Our comprehensive, managed project onboarding ensures a seamless transition.
What is more, we offer complete transparency through weekly and monthly compliance reports.

With connectnet.digital, you have a service delivery partner with two decades of experience simplifying complexities and enhancing protection, leaving you to concentrate on your core business goals. By partnering with us, you are laying the groundwork for a fortified cybersecurity framework.
Our service agreement reaffirms our promise of flexibility, expertise, data security, and quality. With connectnet.digital fully managed Cyber Security, you have the advantage of affordable monthly subscriptions without the shackles of binding contracts.
Our Security Operations Centre and technical team are highly certified, we offer in-country storage of security logs for compliance, and we only use the best-of-breed enterprise solutions delivered as an affordable package.
How are you tracking and managing your Information Technology Risks?
A recent password security study has revealed that 75% of people globally do not follow recommended password best practices. Most people (64%) use weak or repetitive passwords for their online accounts.
The report also found that only 7% of respondents acknowledged password managers as the best method for personal cybersecurity, despite its effectiveness in protecting against phishing attacks and monitoring the dark web for compromised credentials.
Consider Your Current Approach
Are your current defences agile and robust enough to secure your organization's financial and operational stability against evolving cyber threats?
We invite you to explore how our 24x7 Security Operations Centre and Security Information Event Management solutions can enhance your cybersecurity posture.
Don't wait for an incident to jepordise your business. Actively safegaurd your operations today. Join our mailing list for vital security updates and contact us for a no-obligation assessment.
Contact us today
With our CloudConsole nonstop managed security, your journey towards simplified cybersecurity begins here.
Gain the comfort of solid protection without the associated management stress.
Mitigate the risks of inadequate protection, business disruptions, financial losses, and non-compliance.
People, Tools and Advanced ai Technologies making a difference
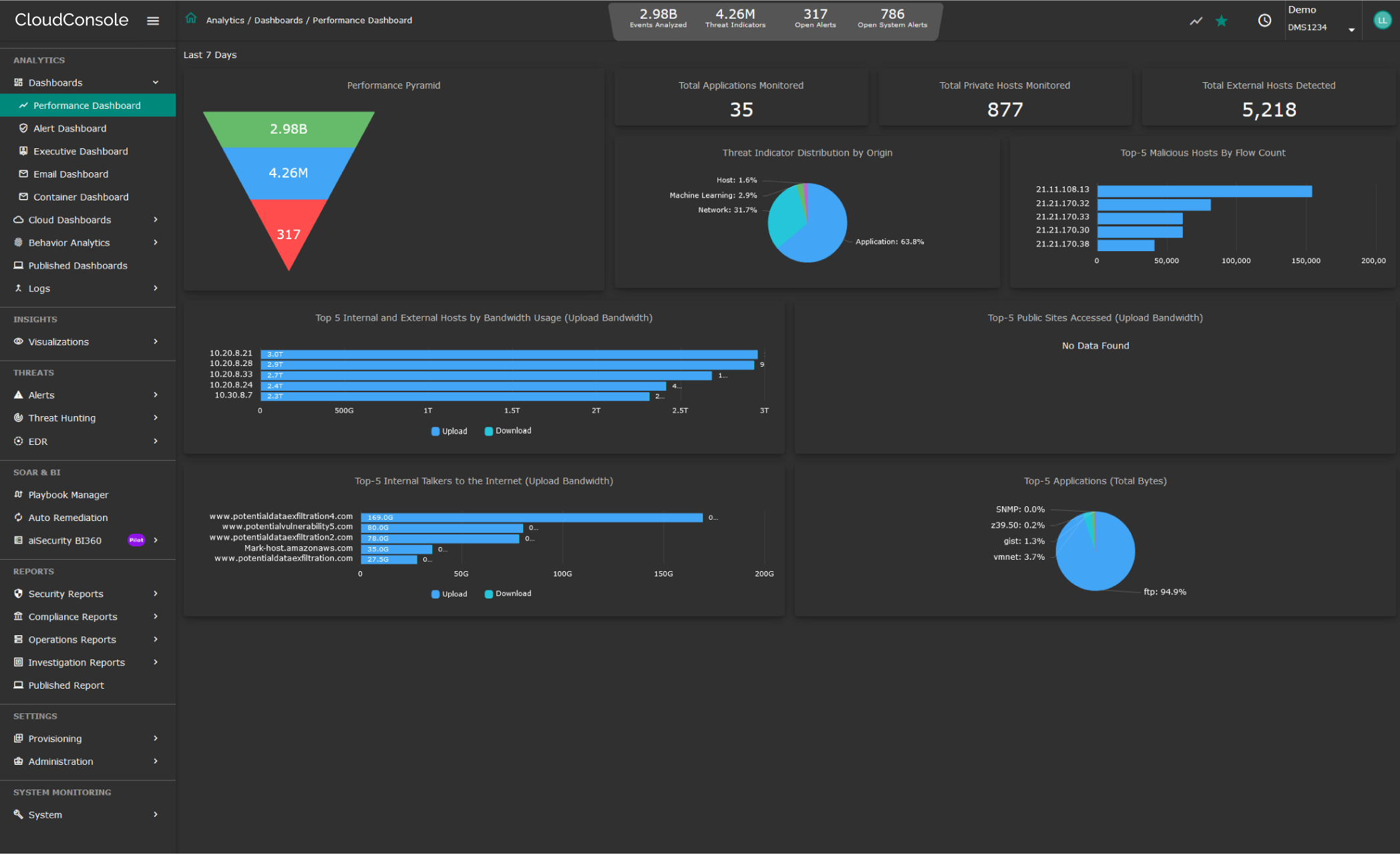
Powerful Security Information Event Management
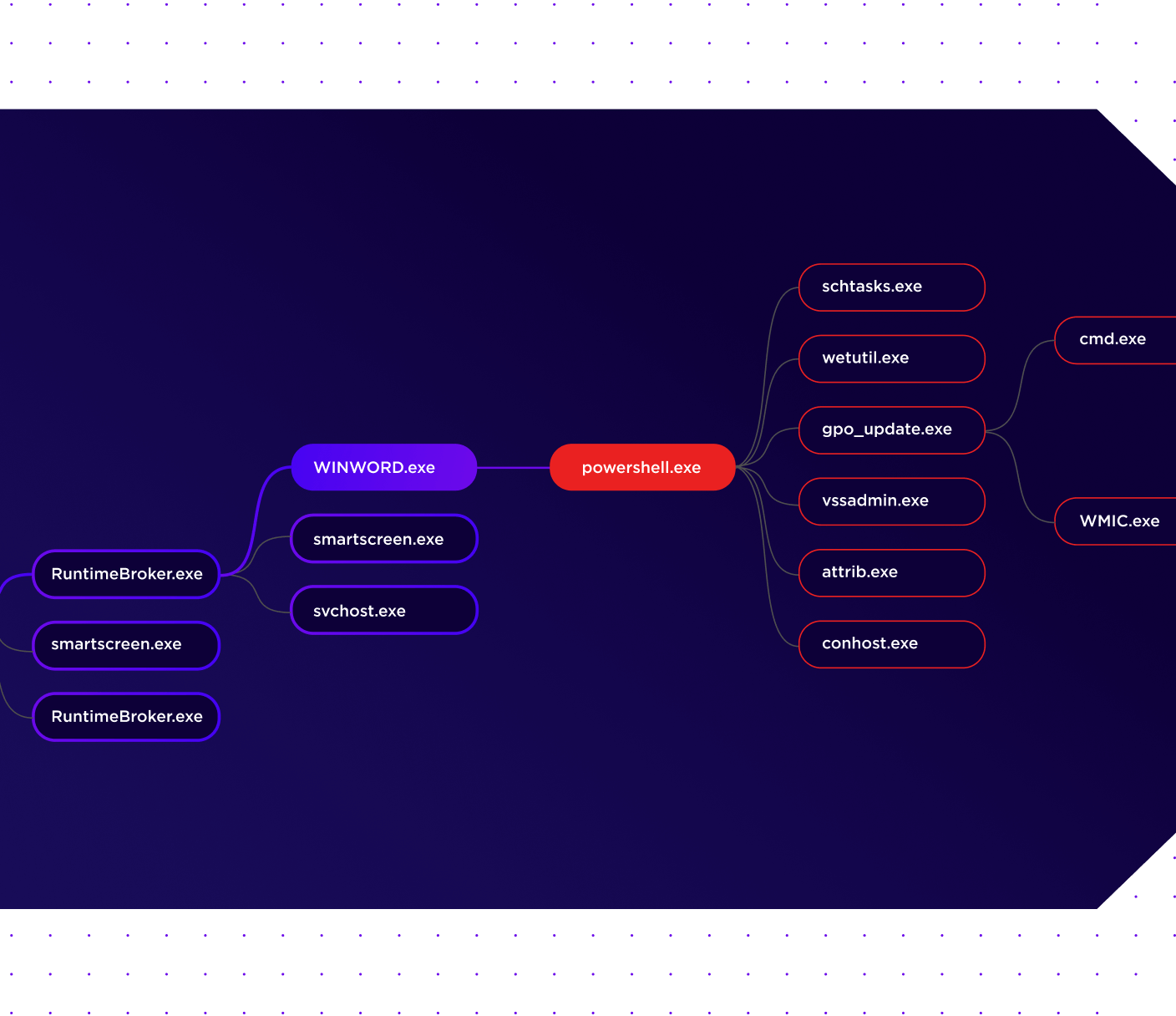
Data Breach detection requires analysis of security related data from multiple angles – file usage, user activity and network traffic (applications, servers). Additionally, threat intelligence and vulnerability scan result plays important role in enriching context, particularly when external perpetrators are involved.
CloudConsole relies on all these datapoints while applying Machine Learning to create a baseline profile and determine deviations with a great degree of confidence. Potential activities, such as port scan, leading to a breach can be correlated in near-real time thus minimizing the scope and scale of breach, saving organizations from economic and reputation loss.
Detecting ransomware requires a high degree of reliance on behavioral analytics and threat modelling to follow various stages of its propagation. Traditional threat detection tools rely heavily on the security analyst to discern unusual activities and create correlation rules to stitch indicators together. This approach heavily weighs on the analyst’s skill in threat detection and fluency with a complex UI, thus leaving a factor of subjectivity in reaching the desired outcome. In sharp contrast, CloudConsole’s aiSIEM/aiXDR leans into Machine Learning for behavioral analytics and Artificial Intelligence for correlating indicators driven by built-in dynamic threat models. When these indicators line up with a certain degree of confidence, the algorithm raises an alert for the analyst to act upon.
Block Attacks on your endpoints
- Dynamic Device Discovery - Automatically identify and protect unmanaged, network-connected endpoints that may introduce new risks.
- Greater Visibility & Actionability - Reduce false positives and increase detection efficacy consistently across OSes with an autonomous, combined EPP+EDR solution.
- Rapid Response & Time to Value - Remediate and rollback endpoints with a single click, reducing mean time to respond and accelerating investigation.